Using WVDAdmin for Azure Windows Virtual Desktop in 2-AAD-Environment (Microsoft Demo Case)
Using Azure Starter for Azure Windows Virtual Desktop in 2-AAD-Environment (Microsoft Demo Case)
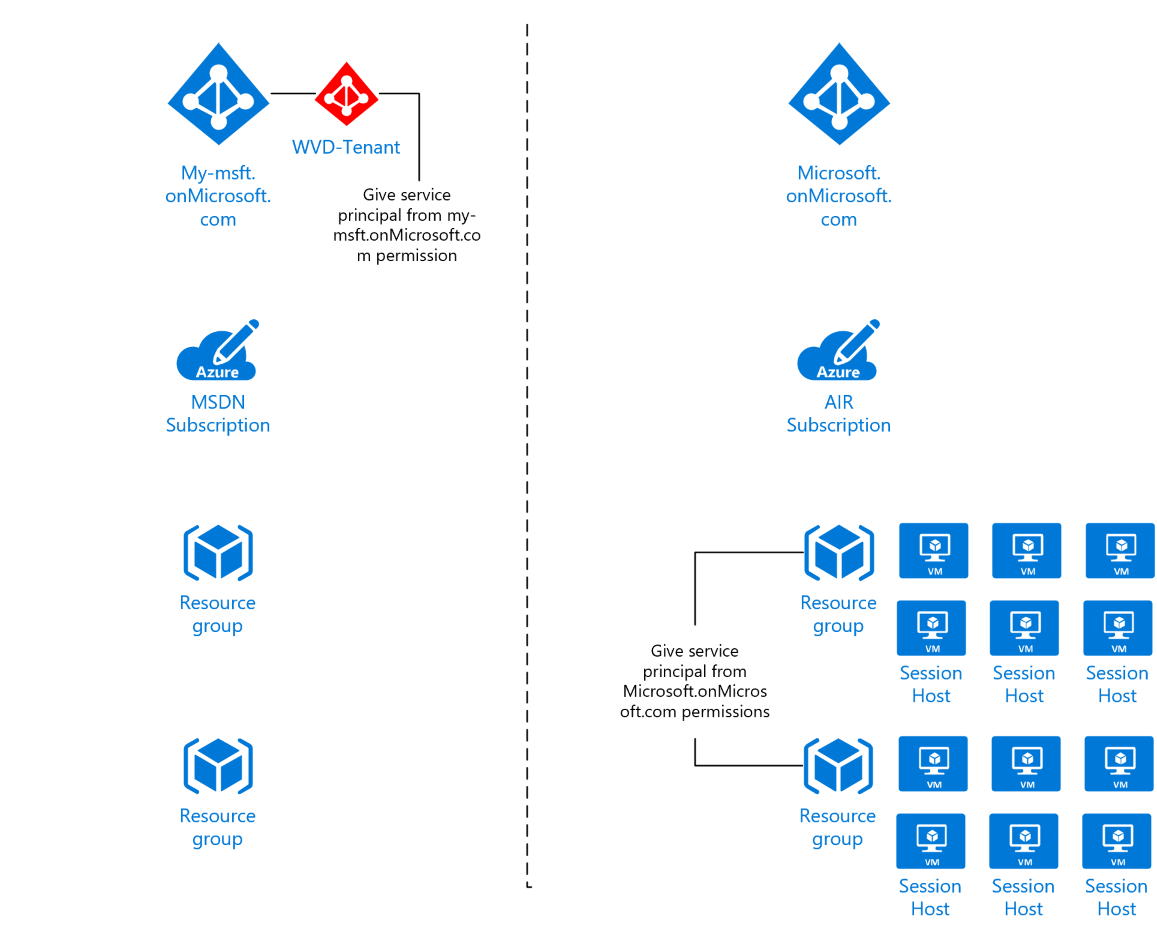
Usually, the WVD/AVD tenant and the resources (sessions hosts) are in the same AAD tenant. If you have two Azure AD tenant, you can use WVDAdmin with a second service principal to access the session hosts.
Example:
- Azure AD 1 - "my-msft.onMicrosoft.com"
- Your personal AAD where you have your users, an AD-Controller, AD-Connect (or AD domain services), and other resources. In this AAD you have deployed your WVD/AVD tenant.
- Azure AD 2 - "microsoft.onMicrosoft.com"
- You have no high-level permission to the AAD because it's own by your company and shared with many other users/professionals. In this AAD, you have a subscription (AIR) containing your session hosts.

Create the first service principal in "my-msft.onMicrosoft.com". Configure this service principal as described in the primary guide - except permitting to the resource group containing the session hosts and the vnet (these are in the other tenant). Use the data of this service principal in the welcom dialog of WVDAdmin.
Create the second service principal in "microsoft.onMicrosoft.com". Give the service principal contributor permission to the resource group containing the session hosts and to the vnet for the session host. Open the registry and navigate to HKEY_CURRENT_USER\Software\ITProCloud\WVDAdmin. Add three string value to configure the service principal to access the resource groups
- AzResAlternativeTenantId
- AzResAlternativeAppId
- AzResAlternativeAppSecret
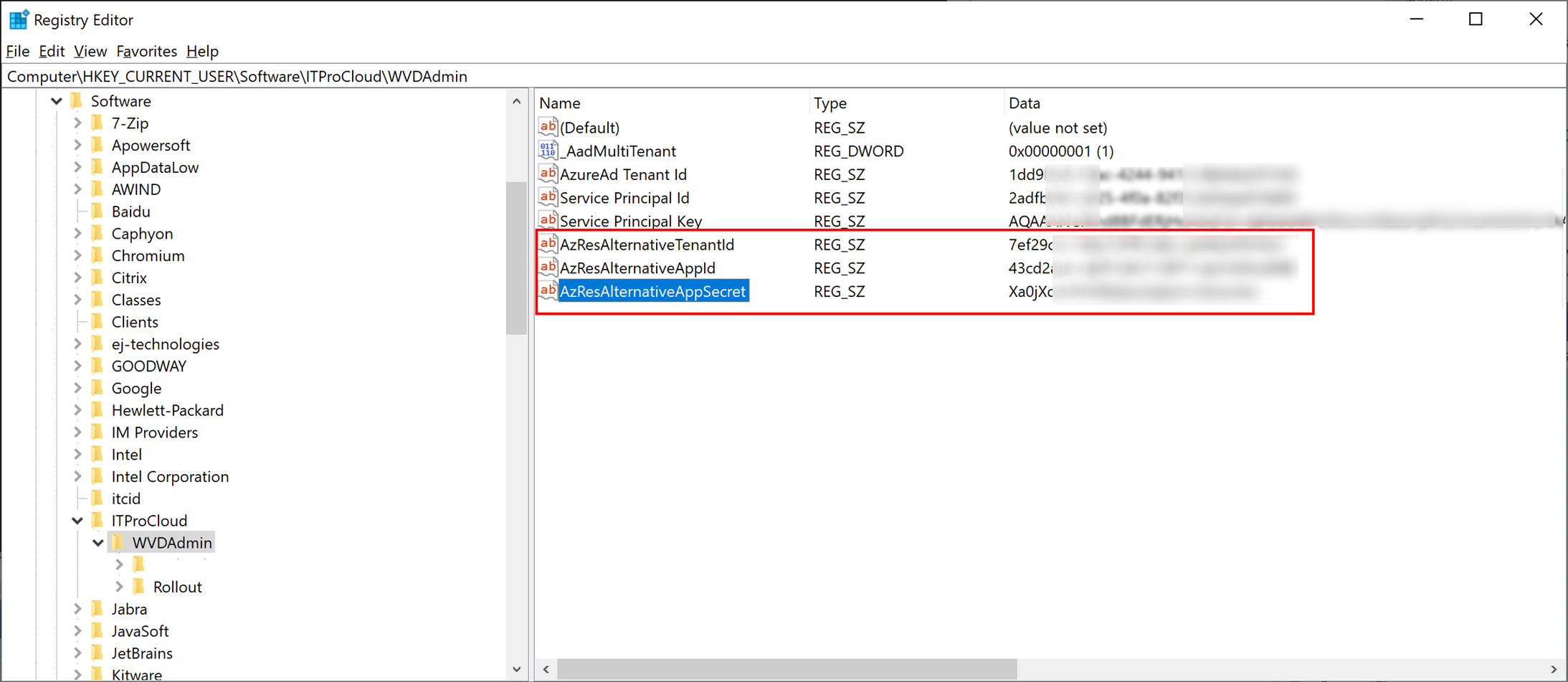
If you use another tenant group name as "Default Tenant Group" add another string "TenantGroupName" and set your tenant group name.
This solution is supported from the current version 1.3.3
Read more and download WVDAdmin on the main page