Honey-Potting in Azure and Unfavorable Account Names
As everybody knows, running a Windows system in Azure unprotected is not a good idea. To get access to an Azure VM, Azure Bastion or VPN are recommended.
But what happens if you deploy a Windows VM in Azure with an unprotected public IP? Several bots try to log on to get access to the VM. For an experiment, I deployed a test VM to Azure with the public IP (my honey pot) to see what happens. Additionally, I wrote a short PowerShell script to search the security log for the logon attempts to get information about the used login names. It is interesting and good to avoid the (sometimes) common terms.
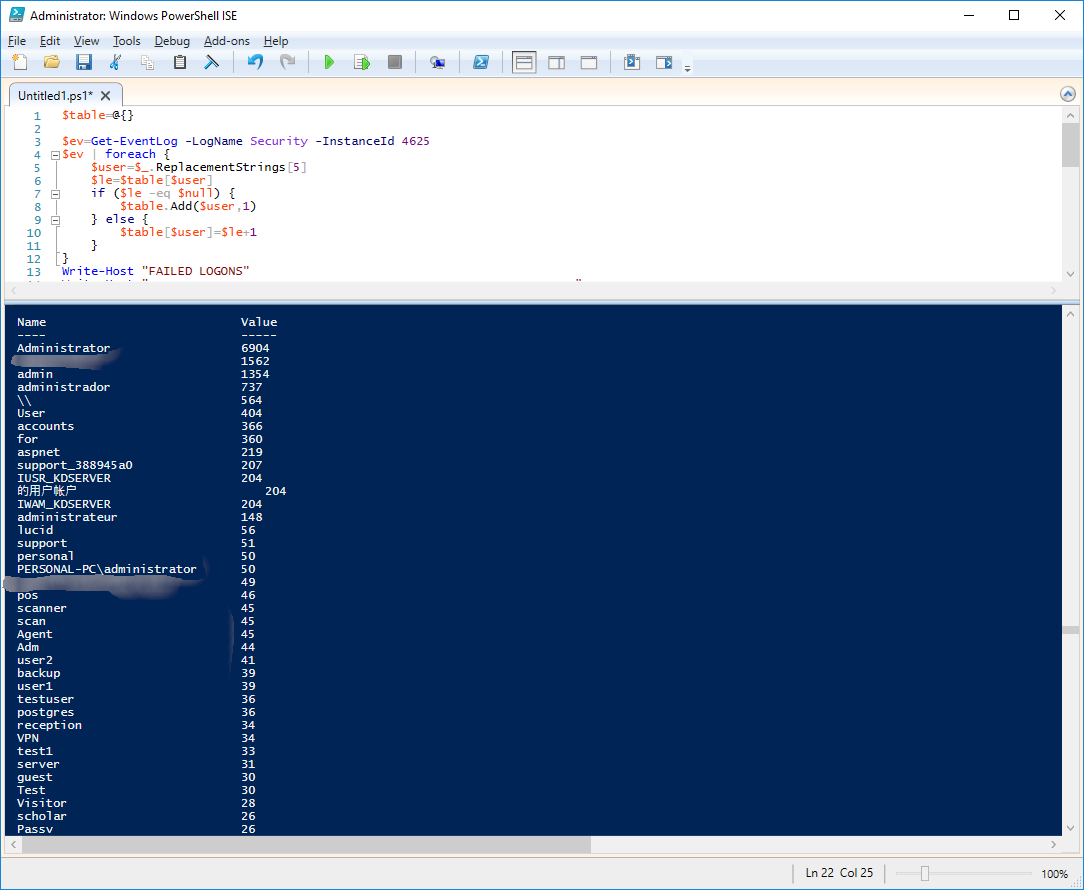
Script (must be run as a local administrator): ``` $table=@{}
$ev=Get-EventLog -LogName Security -InstanceId 4625 $ev | foreach { $user=$_.ReplacementStrings[5] $le=$table[$user] if ($le -eq $null) { $table.Add($user,1) } else { $table[$user]=$le+1 } } Write-Host "FAILED LOGONS" Write-Host "===========================================================" $table.GetEnumerator() | sort Value -Descending
$table=@{} $ev=Get-EventLog -LogName Security -InstanceId 4624 $ev | foreach { $user=$_.ReplacementStrings[5] $le=$table[$user] if ($le -eq $null) { $table.Add($user,1) } else { $table[$user]=$le+1 } } Write-Host "SUCCESSFUL LOGONS" Write-Host "===========================================================" $table.GetEnumerator() | sort Value -Descending
Here is the list of login attempts:
