Securing an app service, a key vault, and a database with private endpoints
A typical Azure application uses an app service representing the front end, a database to store the data and configuration settings, and a key vault to keep secrets (like the connection string to the database). Kommunikation is done encrypted, and the app service has to authenticate to the vault (mostly done via managed identity) and to the database (often done with a connection string).
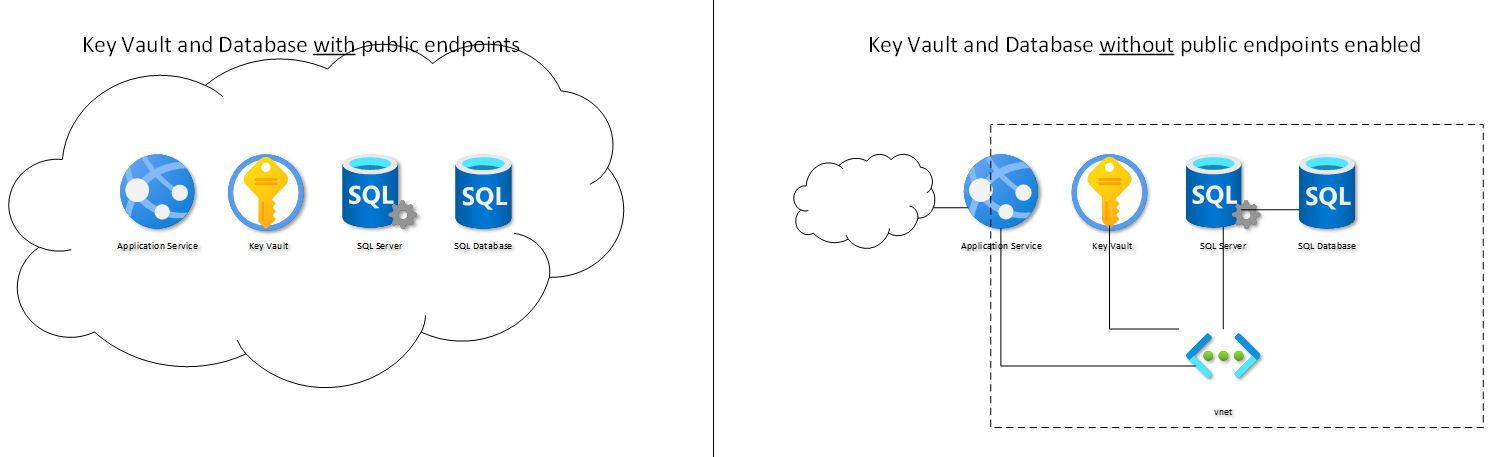
The key vaults and database endpoints are reachable over the public internet. The strong authentication from the app services ensures that the app service gets access.
In some cases, it's mandatory to avoid public access to the vault and the database. Luckily, that can be easily done using private endpoints in Azure. Neither the application nor the configuration of the application needs to be adjusted. So, we can increase the security of any Azure app working with a vault and database (Azure SQL as a service).
I recorded a short video to show the steps. Watch it to the end and avoid my mistake of putting the full IP-range into one subnet (you need two subnets: one for the vault and database and another for the app service).
Check out the video on Youtube: How to secure the database and key vault of an app service / web app in Azure