Azure Virtual Desktop Session Hosts with Azure Disk Encryption
Hydra for Azure Virtual Desktop and WVDAdmin are supporting ADE for AVD Session Hosts.
Azure Disk Encryption (ADE) encrypts the OS and data disks of Azure virtual machines (VMs) inside your VMs by using BitLocker. ADE cannot be combined with a disk encryption set.
To roll out session hosts with ADE in Hydra, some resources must be prepared to work: Azure Key Vault with an encryption key, and Azure Key Vault to store the secrets of the disks (can be the same vault)
- First, create a Key Vault in the Azure Portal
- Give the service principal (from the tenant configuration) contributor permission to the vault (access and control)
- In Access Policies, give the service principal the following permissions: -- Key permissions: Get, Encrypt, Wrap Key -- Secret permissions: Set
- Check the boxes: Azure Virtual Machines for deployment and Azure Disk Encryption for volume encryption
- Give yourself permissions: Key and secret management
- Go to Keys and click on Generate. Type a name and select RSA and 2048
- Click on the generate key and on the current version. Copy the Key identifier (must include the version). E.g., https://
.vault.azure.net/keys/ADE-Encryption/bf270e977a574813a87bb637d57a6675
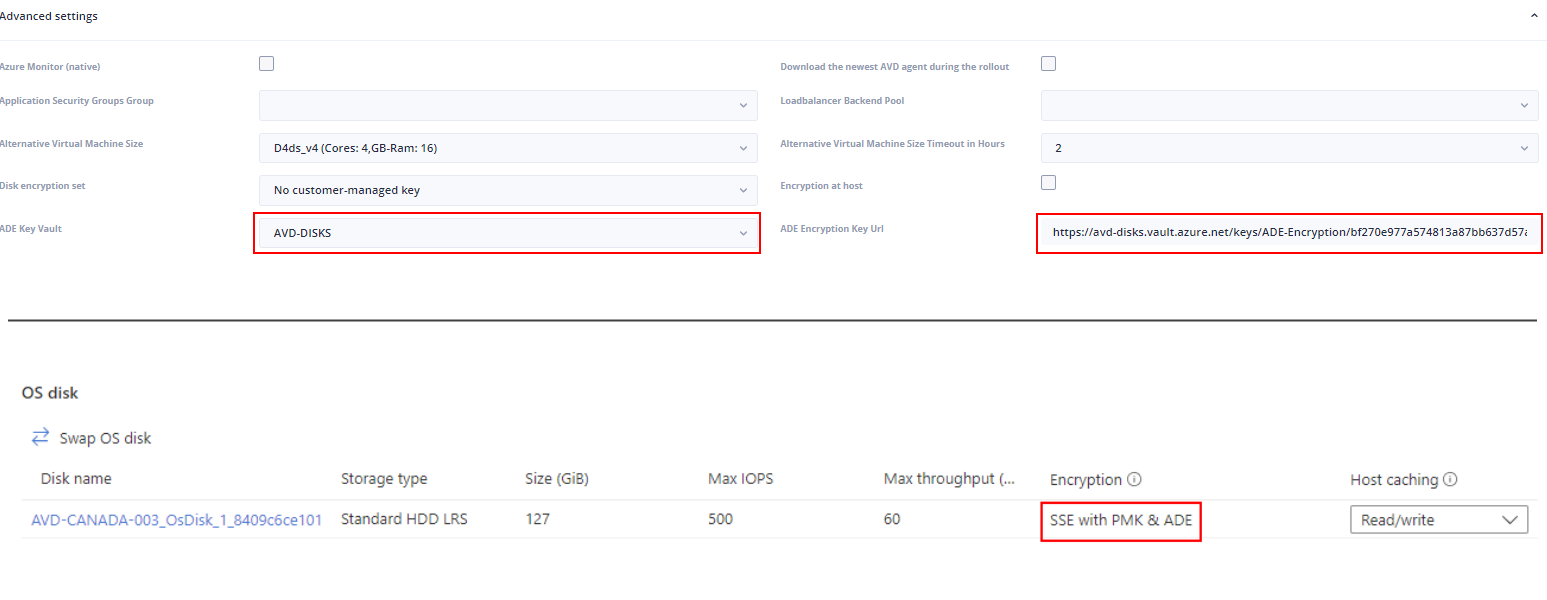
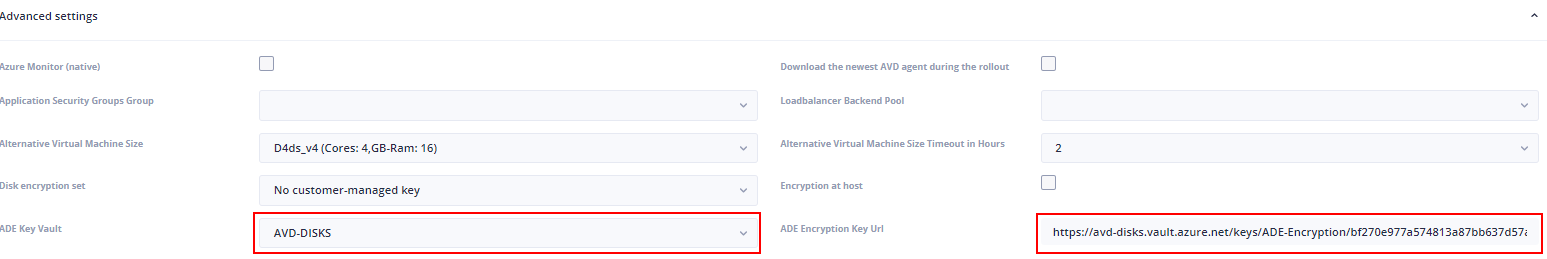
In Hydra, configure "New Session Host Rollout": In "Advanced settings" select the Key Vault in ADE Key Vault Copy the Key Identifier to ADE Encryption Key Url
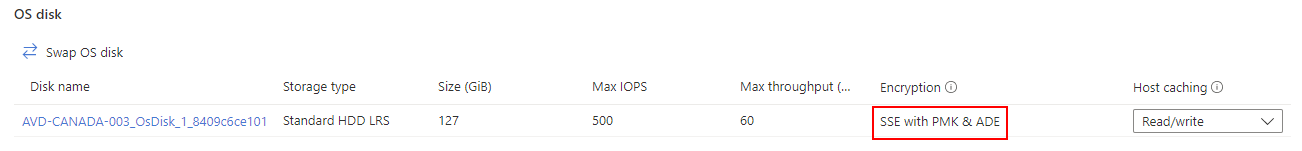
Do a deployment to verify that the disk is ADE encrypted:
To rollout hosts with ADE with WVDAdmin, add tags to the host pool:
WVD.Default.KeyVault.Id: resource id of the KeyVault (/subscriptions/